Answer all questions from this section in the spaces provided
1.List the components of a computer system hardware. (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
2.Describe the term key to storage systems (1 Mark)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
3.One classification of software is system software (a)
i. What is meant by system software (1 Mark)
…………………………………………………………………………………………………………………………………………………………………………………..…………………………………………..
ii. Give one example of system software. (1 Mark)
……………………………………………………………………………………………………………………………………………………………..……………………….……………………………………….
(b)
i. Name one other software classification (1 Mark)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
ii. Give one example of this type of software (1 Mark)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
4 a. What do you understand by the term database management system? (DBMS)
? (1 Mark)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………….
b. Define the following terms as used in a database. (2 Marks)
i. Primary Key ………………………………………………………………………………………………………………
ii. Record ………………………………………………………………………………………………………………
5.Differentiate between COMports and LPT ports (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
6.List three factors to consider when deciding on the choice of electronic data processing method (3 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… 7.Ventilation is an important practice in the computer lab because it enhances proper circulation of air. Outline three ways in which air is regulated in the computer room. (3 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… 8.What do the following control measures against computer crime involve? (4 Marks)
Audit trail ………………………………………………………………………………………………………………. Data encryption ……………………………………………………………………………………………………………….. Log files …………………………………………………………………………………………………………… Passwords ……………………………………………………………………………………………………………
9.Highlight the use of find and replace features in word processors. (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
10.Explain why two’s complement is preferred to one’s complement in computing. (1 mark)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………
11.Computers have evolved through a number of generations.
List any three characteristics of the first generation of computers. (3 marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… 12.List four formatting techniques used in Ms excel (2 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….
13.List four examples of flat panel displays. (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………
14.Explain the following terms as used in the word processing. (4 Marks)
Indenting ………………………………………………………………………………………………………………. Alignment ………………………………………………………………………………………………………………. Footnote ………………………………………………………………………………………………………………. Endnote ………………………………………………………………………………………………………………..
15.Describe the role of an operating system in Memory management ……………………………………………………………………………………………………………….. ii. Job scheduling ………………………………………………………………………………………………………………… iii. Error handling ……………………………………………………………………………………………………………….. iv. Resource control ………………………………………………………………………………………………………………
SECTION B (60 MARKS)
16 a. State the three basic types of program control structures. (3 Marks)
…………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………….. b. Draw a flowchart which will simulate the processing of student’s report.
The simulation should be such that the user repeatedly inputs marks per subject for six subjects using a looping control structure.
The computer processes the total marks and mean score of the student.
NOTE:
1. It is assumed that the student does six subjects
2. The output required are: Average score and total marks
c. Differentiate between analogue and digital data. (2 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… d. Outline three advantages of using computers for data processing over other types of office and business equipment. ……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… 17 a. Convert the following numbers to their decimal equivalent. (6 Marks)
i. 11.0112 ……………………………………………………………………………………………………………………………………………………………………………………………………………………………… ii. 12.158 ……………………………………………………………………………………………………………………………………………………………………………………………………………………………… iii. A3.3/6 ……………………………………………………………………………………………………………………………………………………………………………………………………………………………… b. Outline four ways in which data integrity may be maintained. (4 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………. c. Explain four advantages of using questionnaires as a fact finding tool. (4 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… d. What is the role of a recycle bin? (1 Mark)
……………………………………………………………………………………………………………… 18 a. Masai teacher’s college has decided to automate its library for effective services to the students. Identify four methods they are likely to use to gather information during system development. (4 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………. b. What do the following terms mean in relation to internet? (4 Marks)
i. Downloading ……………………………………………………………………………………………………………….. ii. Hyperlink ……………………………………………………………………………………………………………….. iii. Web browsers ………………………………………………………………………………………………………………. (iv)
Internet service providers ……………………………………………………………………………………………………………… c. Differentiate between sorting and filtering as used in electronic spreadsheet program (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………. d. What do the following terms mean i. Spam mail ……………………………………………………………………………………………………………………………………………………………………………………………………………………………… ii. Disk ……………………………………………………………………………………………………………………………………………………………………………………………………………………………… iii. Onboard moderm ……………………………………………………………………………………………………………………………………………………………………………………………………………………………… e. What does the term WIMP mean as used in computing? …………………………………………………………………………………………………………………………………………………………………………………………………………………………….. 19.(a)
Define a database model (1Mark)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………… b. List four advantages of using database systems (2marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… c. In a database system, data integrity ensures the correctness and completeness of the data in the database.
Differentiate the following types of integrity constraints:
i. Validity integrity (1mark)
……………………………………………………………………………………………………………… ii. Entity integrity (1mark)
………………………………………………………………………………………………………………. iii. Referential integrity (1mark)
……………………………………………………………………………………………………………… d. Briefly describe the three database models (3 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… e. Using diagrams describe the following three types of relationships. (3Marks)
i. One – to – one
ii. One – to – many
iii. Many – to – many
f. File organization refers to the arrangement of records on secondary storage.
Briefly describe the following file organization methods. (3 Marks)
Serial ………………………………………………………………………………………………………….. Sequential …………………………………………………………………………………………………………. Random ………………………………………………………………………………………………………….. 20. a. Your School has decided to replace its library control system.
The current system was implemented ten years ago but has restricted reporting facilities and has a text – based interface.
The school intends to replace the old system with a new computerized system, and is now considering both ‘parallel running ‘ and ‘direct changeover’ Briefly explain the terms parallel running and direct change over as used in system implementation. (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………… ii. Give two disadvantages of direct changeover over parallel running (1 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………….. iii. Identify two main risks of direct changeover during system implementation (2 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………… iv. Mention any two advantages of running both the manual system and the computerized system simultaneously (2 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………….………………………….. b. i. What is a website? (2 marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………… ii. Name three facilities that are needed to connect to the internet. (3 Marks)
……………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………… c. State three ways students can benefit by having internet in a school (3 Marks)
………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………………
Marking Scheme
1.List the components of a computer system hardware. (2 Marks)Input – accepts in data and converts it into computer understandable formProcessor – manipulates data into informationStorage – holds data, instruction and information in the computer.Output – gives the results of processing to the user
2.Describe the term key to storage systems (1 Mark)
These are microcomputers – based systems that take in data from the VRU (Keyboard, mouse and monitor) and store it in diskettes
3.One classification of software is system software
(a)
i. What is meant by system software (1 Mark)System software refers to the programs that control the performance of the computer.
ii. Give one example of system software. (1 Mark)
Utility programs, O/S, compilers and interpreters
(b)i. Name one other software classification (1 Mark)Application software
ii. Give one example of this type of software (1 Mark)Word processors, spreadsheet, RBMS
4 a. What do you understand by the term database management system? (DBMS)? (1 Mark)DBMS – collection of data programs (software) that help one retrieve data and perform operations on it.
It involves creating, modifying, deleting and adding data files and using this data to generate reports.
b. Define the following terms as used in a database. (2 Marks)
i. Primary KeyAn attribute of a relation that uniquely identifies all the other attributes
ii. Recordcollection of related fields (data items)
5.Differentiate between Comport and LPT ports (2 Marks)Com – ports are used for serial cablesLPT ports are used for parallel cables connection
6.List three factors to consider when deciding on the choice of electronic data processing method (3 Marks)
\\Suitability of accumulating dataResponse timeCost of initial installation and operationsEase of development and subsequent maintenance
7.Ventilation is an important practice in the computer lab because it enhances proper circulation of air.Avoid overcrowding of either machines or users in the roomEnsuring that the room has enough ventilation points like windowsInstalling air conditioners
Outline three ways in which air is regulated in the computer room. (3 Marks)Avoid overcrowding of either machines or users in the roomEnsuring that the room has enough ventilation points like windowsInstalling air conditioners
8.What do the following control measures against computer crime involve? (4 Marks)
Audit trail
Careful study of an information system by experts to establish all weaknesses in a system that could lead to security threat.
Data encryptionCombination of letters and characters that deter unauthorized access
Log files Passwords
Combination of characters that deter unauthorized user from accessing data.
9.Highlight the use of find and replace features in word processors. (2 Marks)It is used to look for specified words in a document and replacing them with alternative.
10.Explain why two’s complement is preferred to one’s complement in computing. (1 mark)There is only one way of representing a zero unlike in ones compliment.
11.Computers have evolved through a number of generations.
List any three characteristics of the first generation of computers. (3 marks)Large in physical sizeUsed thermionic valvesConsumed a lot of powerConstant breakdownLow memory and processing speedCost was high
12.List four formatting techniques used in Ms excel (2 Marks)Change text colourChange font sizeChange font styleText alignment
13.List four examples of flat panel displays. (2 Marks)Gas plasmaElectro luminiscentThin film transistorsLiquid crystal display
14.Explain the following terms as used in the word processing. (4 Marks)
IndentingMove text away from the left margin
Alignmentplacing text on page relative to right, left or centre of the page
FootnoteAdditional piece of information printed at bottom of page
Endnotenotes collected under separate heading at end of chapter in a document
15.Describe the role of an operating system in
Memory management
Load application programs from external storage in to main memory. Also note the part of main memory in use and free
ii. Job scheduling
Prepares jobs for continuous execution determining the first task to be done and last one.
iii. Error handling
Reports errors that occur during execution
iv. Resource control
Control use computer hardware by system software and application programs
SECTION B (60 MARKS)
16 a. State the three basic types of program control structures. (3 Marks)SequenceSelectionIteration
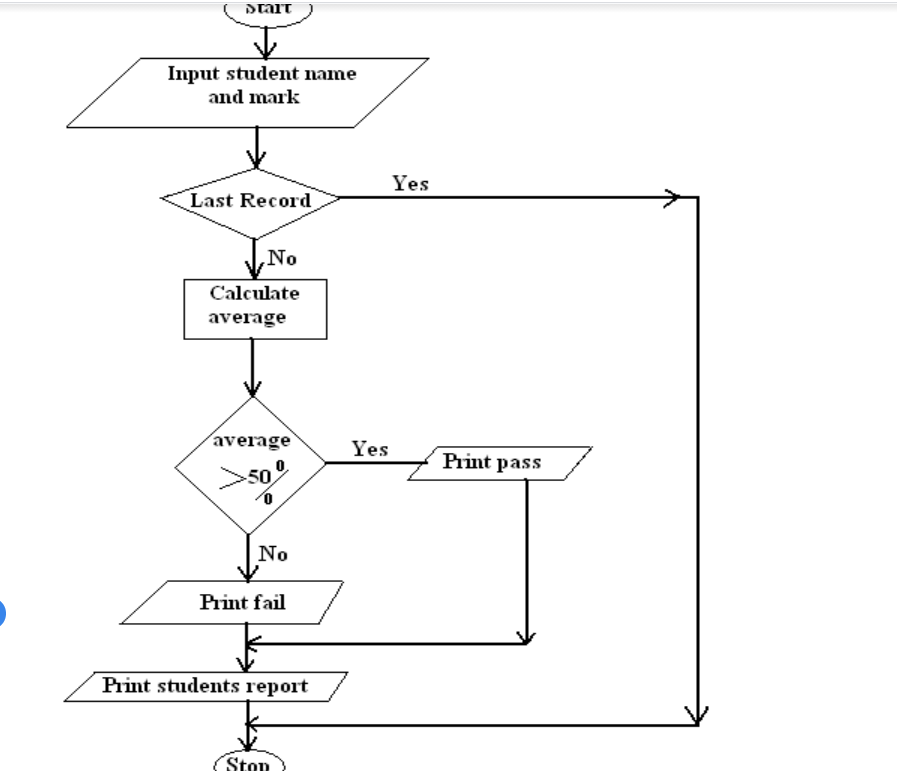
b. Draw a flowchart which will simulate the processing of student’s report.
The simulation should be such that the user repeatedly inputs marks per subject for six subjects using a looping control structure.
The computer processes the total marks and mean score of the student.
NOTE:
1. It is assumed that the student does six subjects
2. The output required are: Average score and total marks
c. Differentiate between analogue and digital data. (2 Marks)
Analog is continuous in nature. While digital is discrete in form
d. Outline three advantages of using computers for data processing over other types of office and business equipment.Computers are fastProduce more accurate resultsProduce neat workAre more efficient
17 a. Convert the following numbers to their decimal equivalent. (6 Marks)
i. 11.0112
ii. 12.158
iii. A3.3/6
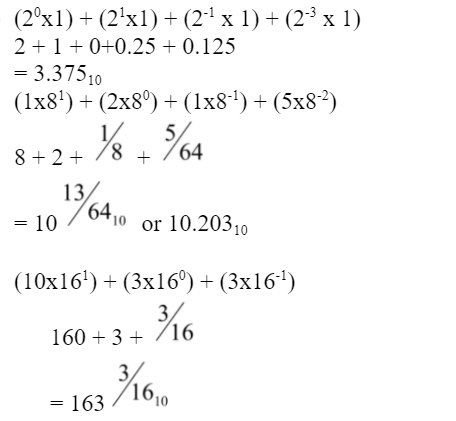
b. Outline four ways in which data integrity may be maintained. (4 Marks)Back up dataControl data accessDesign interface that minimize invalid data entryUse data capture service
c. Explain four advantages of using questionnaires as a fact finding tool. (4 Marks)
Can reach many respondentsGive many responsesSaves timeMinimjze biasness
d. What is the role of a recycle bin? (1 Mark)
Contain the deleted files
18 a. Masai teacher’s college has decided to automate its library for effective services to the students.
Identify four methods they are likely to use to gather information during system development. (4 Marks)QuestionnairesInterviewsObservationsNote takingStudy available documentsTape recording
b. What do the following terms mean in relation to internet? (4 Marks)
i. Downloading
Process of transferring information from remote computer to local storage.
ii. Hyperlink
Text or picture in an electronic document
iii. Web browsers
Applications that enable a person to access the internet.
(iv)
Internet service providers
Companies that offer internet services to end users.
c. Differentiate between sorting and filtering as used in electronic spreadsheet program (2 Marks)
Sort is to arrange data in a predefined order either ascending or descending. While filtering is a quick and efficient method of finding and working with a subject within a list.
d. What do the following terms mean
i. Spam mail
A mail sent to many people indiscriminately.
ii. Disk
Flat circular plate covered in a magnetic which is able to store data on concentric tracks.
iii. Onboard moderm
Modem fixed on mother board
e. What does the term WIMP mean as used in computing?
Windows icons mouse and pointing devices
19.(a) Define a database model (1Mark)
The arrangement of data in a file which determine the access method.
b. List four advantages of using database systems (2marks)Control of data redundancyMaintain data consistencySharing of dataImproved date integrityEconomy of scaleImproved security
c. In a database system, data integrity ensures the correctness and completeness of the data in the database.
Differentiate the following types of integrity constraints:
i. Validity integrity (1mark)
Ensure that the data fields contain the correct data type
ii. Entity integrity (1mark)
Primary key cannot have empty values.
iii. Referential integrity (1mark)
A foreign key can only have the values of the relevant primary key.
d. Briefly describe the three database models (3 Marks)Hierarchical model – Records in the database can be related in one parent only but can have more child records.Network – any record can be related with any other record.Relational model – all data is logically structured within tables.
e. Using diagrams describe the following three types of relationships. (3Marks)
i. One – to – one
One to one – for any member of A there is only one member of B and for any member in B there is one member of A.
ii. One – to – many
One to many – for a single member of A, there may be multiple associations with it B but for any B member there is only one member of A associated with it.
iii. Many – to – many
Many to many – for member in A there may be more members of B and for any member in B there may be many members of A
f. File organization refers to the arrangement of records on secondary storage.
Briefly describe the following file organization methods. (3 Marks)
SerialRecords are placed on the disk with no particular order.
SequentialRecords are placed on disk according to a specific field
RandomA hash function calculates the address of the page in which the record is to be stored based on one or more of the fields.
20. a. Your School has decided to replace its library control system.
The current system was implemented ten years ago but has restricted reporting facilities and has a text – based interface.
The school intends to replace the old system with a new computerized system, and is now considering both ‘parallel running ‘ and ‘direct changeover’
Briefly explain the terms parallel running and direct change over as used in system implementation. (2 Marks)
A hash function calculates the address of the page in which the record is to be stored based on one or more of the fields.
ii. Give two disadvantages of direct changeover over parallel running (1 Marks)It may be inconveniencing incase the new system fails/face problem. -The users may not have gained enough confidence to run the new system.
iii. Identify two main risks of direct changeover during system implementation (2 Marks)Incase of system failureIf testing was not thoroughly done.Requires training on new programsRequires new hardware and software (costs)
iv. Mention any two advantages of running both the manual system and the computerized system simultaneously (2 Marks)Promotes confidence as a result of same input and outputTraining is done to enable familiarizationReliable in terms of testing
b. i. What is a website? (2 marks)
Collection /group of related WebPages belonging to an organization or individual
ii. Name three facilities that are needed to connect to the internet. (3 Marks)Internet softwareTelecommunication facilitiesModemInternet service providerTCP/IP protocol
c. State three ways students can benefit by having internet in a school (3 Marks)Exchange programs with students in other schoolsE-learningResearch widelyf

